In this bog post I’m sharing a guide on how to create a new Firewall Rule with PowerShell. We’ll create a new inbound rule using a PowerShell script for the local Windows Firewall, to allow SQL Server (port 1433).
Script to Create a New Firewall Rule for SQL Server
The PowerShell script below creates a new inbound rule on the local server which allows port 1433 (default Microsoft SQL Server port). It ensures that only devices from a specific subnet (e.g., 10.19.24.0/24) can access SQL Server.
Before running the script, make sure to open PowerShell as Administrator, otherwise the script won’t execute.
# Define the allowed IP range (Modify as needed)
$AllowedIPRange = "10.19.24.0/24"
# Check if the rule already exists; if not, create it
if (-not (Get-NetFirewallRule -DisplayName "Allow Inbound SQL (1433)" -ErrorAction SilentlyContinue)) {
New-NetFirewallRule `
-DisplayName "Allow Inbound SQL - 1433" `
-Direction Inbound `
-Protocol TCP `
-LocalPort 1433 `
-Action Allow `
-RemoteAddress $AllowedIPRange
}
This script is checking if the Firewall Rule already exists before creating it.
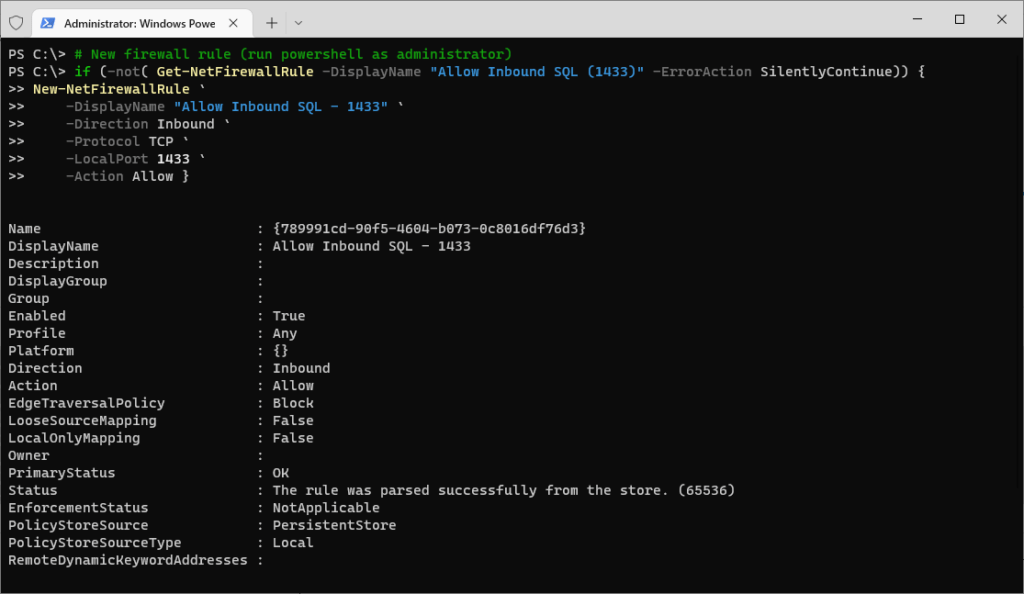
For better security, always restrict firewall rules to trusted IP ranges instead of allowing all inbound traffic. The screenshot shows allowing all IPs on 1433, if troubleshooting an issue you could temporarily disable the Windows Firewall and quickly perform your connection test.
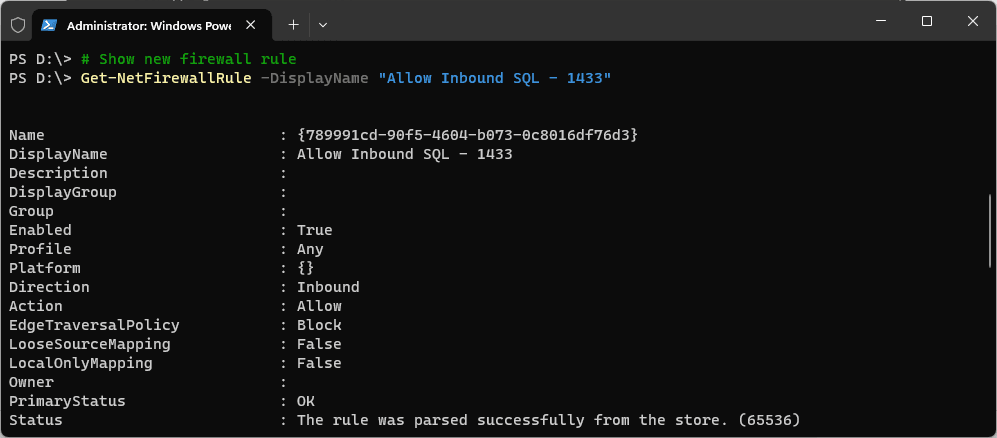
To view your newly created Firewall rule, we can use the Get-NetFirewallRule cmdlet:
Relevant MS Docs:
– New-NetFirewallRule
– Set-NetFirewallRule
– Remove-NetFirewallRule
I seem to write about the Windows Firewall often enough for it to have a blog tag on here. Feel free to check out my other Firewall related posts for more info as linked!
One other thing to add to this is, if you’re working within a Corporate environment, you might need to ask network teams to open up network flow between servers. For more information on this, checkout my other blog post: How to Test Connectivity to Remote Server Ports with PowerShell
Leave a Reply