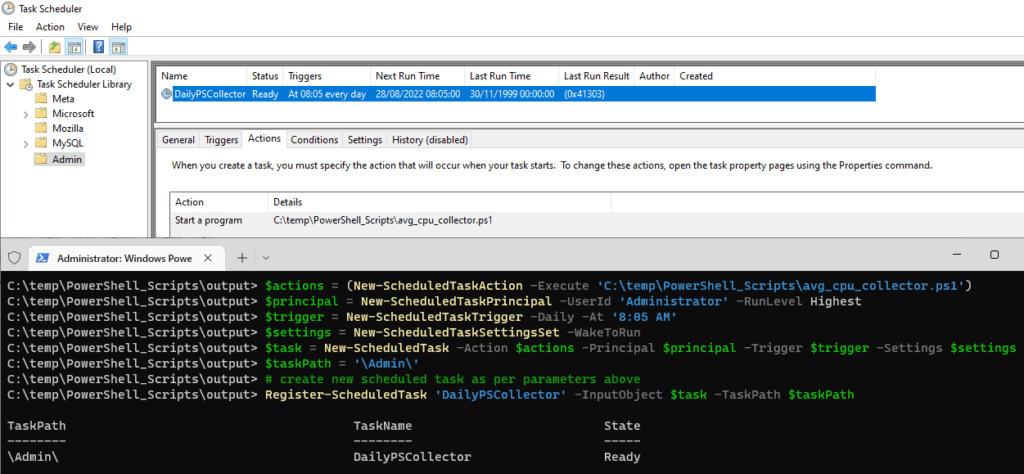
To get environment variables in PowerShell, we can use Get-ChildItem env: to list all the environment variables and $env: to return the value of a specific environment variable. This blog post should help explain this as well as how to set new values for Environment Variables.
An environment variable is a value that is stored on a computer and can be accessed and used by programs to alter their behaviour. For example, in the AWS CLI you can set an environment variable called “AWS_REGION” and assign it a value such as “eu-west-1”. Then, you could have a program that reads this environment variable and uses it to specify the AWS region when making API requests.
In PowerShell, you can access environment variables using a number of different cmdlets. This post covers cover two of the most common methods, Get-ChildItem and Get-Item.
This post will cover the following:
– List All Environment Variables
– Get Value of a Specific Environment Variable
– Set New Environment Variable
List All Environment Variables
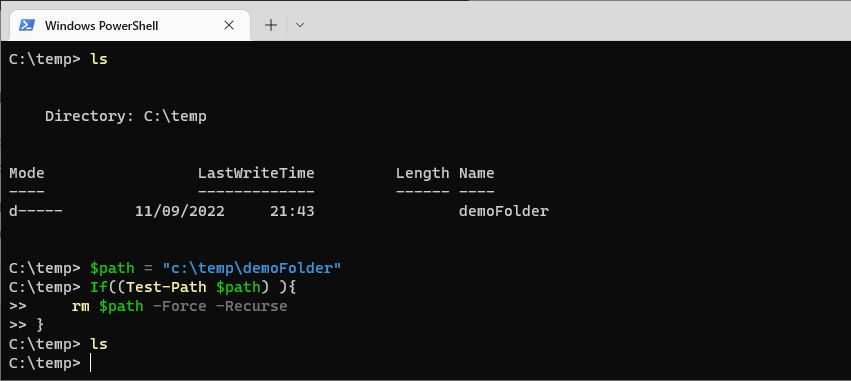
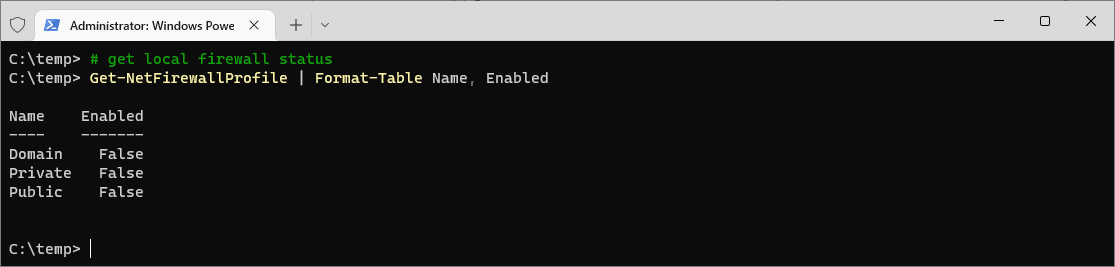
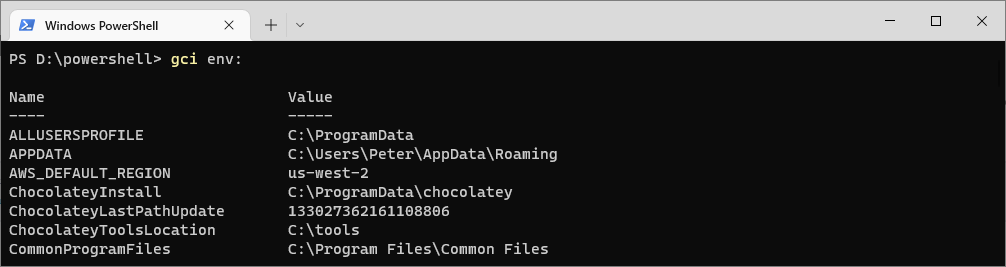
To list all of the environment variables on your system, use the Get-ChildItem cmdlet with the Env: drive. This displays a list of all the environment variables and their current values.
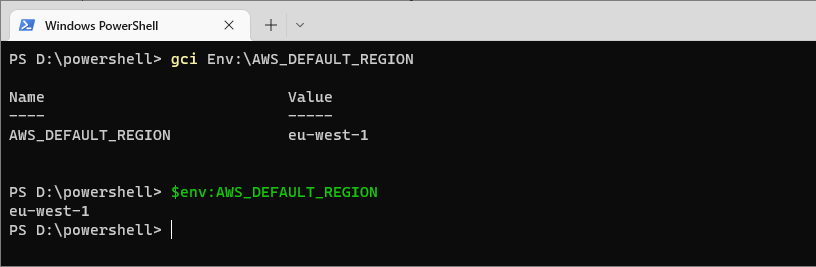
You can also run gci which is an alias for Get-ChildItem as displayed in my screenshots below.
# List all environment variables Get-ChildItem Env:
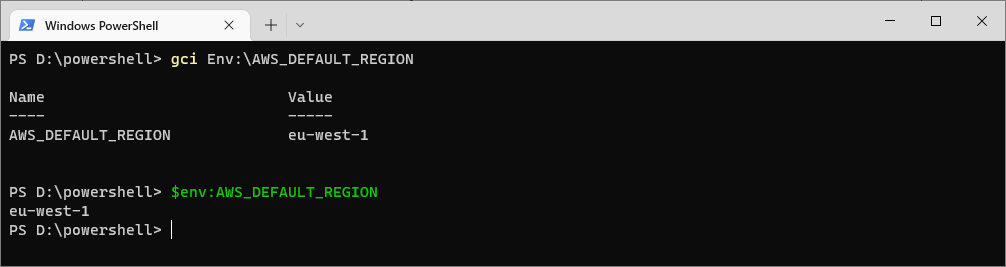
Get Value of a Specific Environment Variable
To return the value of an environment variable in PowerShell, run the following:
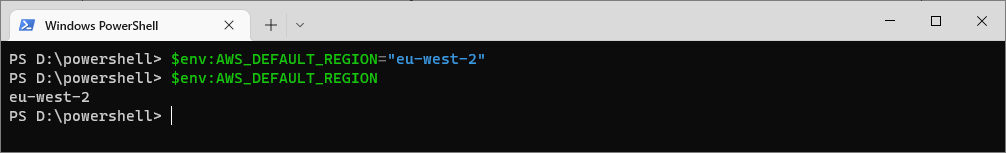
# Get the value of the aws_default_region environment variable gci Env:\AWS_DEFAULT_REGION # Do the same but alt (easier) syntax $env:AWS_DEFAULT_REGION
Set New Environment Variable
To set a new value for the AWS_DEFAULT_REGION environment variable with PowerShell, use the following command:
# Set the AWS Default Region Environment Variable $env:AWS_DEFAULT_REGION="eu-west-2"